Saturday, 10 September 2011
IStealer 3.0 [Tutorial] [Download]
![[Image: istealer.jpg]](http://img26.imageshack.us/img26/9679/istealer.jpg)
Before we start, I just wanted to say this, This is tutorial for people which have no knowledge on configuring a iStealer server! If you have no knowledge on how to configure a iStealer server please read on!!
Also before we start we need to sign up for a free FTP service, I currently usehttp://www.drivehq.com so use that one, sign up and now lets start!
Labels:
Downloads,
Free,
Hacking,
RAT Programming,
Software
Avast! Free Antivirus 6.0.989 Beta
Avast! Free Antivirus - Free Antivirus Avast, whose work is based on a number of award-winning antivirus kernel of avast!, includes all the features that you would expect from a modern antivirus program. In particular, it includes technology to protect against "spyware, " a certified West Coast Labs Checkmark, module protection against rootkits and reliable self-defense module. And the latest version provides even more high speed scanning and advanced malware detection. The program includes several of real-time "screens" that continuously monitor your email and connect to the Internet, checking the files to your computer every time they are opened or closed.
Antivirus avast! Free Antivirus is equipped with a completely revamped user interface that greatly simplifies the anti-virus scanning. With proper use Avast in conjunction with programs such as utilities for data backup, the program significantly reduces the risk that your computer is exposed to viruses or will be infected by them.
TrustPort Antivirus 2011
TrustPort Antivirus (2011) v11.0.0.4615 Final | 193.7 MB
TrustPort Antivirus 2011 - is a universal dvuskanernym antivirus solution that can withstand millions of spreading worldwide network of Internet threats - viruses, worms, spyware and Trojans. Due to regular updating of anti-virus and universal technology heuristics, TrustPort Antivirus has stopped suschestvuyushie malware, and those that will be created.
Friday, 9 September 2011
REFOG Keylogger v6.0.4.1014 + Serial [ Full Version ] [Crack]
Concerned About Your Children Safety?
If your kids spend time chatting or playing computer games, they can be approached or threatened by the strangers. Internet has anonymity, and anonymity means impunity in the minds of molesters. The solution? Violate their anonymity by monitoring your kids’ activities!
REFOG Personal Monitor is designed to deal with extended families, but it fits small families just as easy. Allowing you to monitor your children activities remotely over the Internet, REFOG Personal Monitor does not even require your close presence in order to be alerted about suspicious activities of either your children or someone they chat with.
Hiren’s BootCD 13.2

Genre: SYSTEM Tools
Hiren's Boot CD is a boot CD containing various diagnostic programs such as partitioning agents, system performance benchmarks, disk cloning and imaging tools, data recovery tools, MBR tools, BIOS tools, and many others for fixing various computer problems. It is a Bootable CD; thus, it can be useful even if the primary operating system cannot be booted. Hiren's Boot CD has an extensive list of software. Utilities with similar functionality on the CD are grouped together and seem redundant; however, they present choices through UI differences.
Changes From Version 13.1 to 13.2
New Added Softwares:
Labels:
Downloads,
Free,
Hiren Boot CD,
Tools
Advance SQL Injection - 17 DefCon [Video]
According to OWASP top 10 vulnerabilities of 2010, SQL injection is the most dangerous and most common vulnerability around, A SQL Injection vulnerability occurs due to improper input validation or no input validation at all, what I mean by improper or no input validation is the user input is not filtered(for escape characters) before it gets passed to the SQL database, A Sql injection attack can be any many forms, but it's usually categorized into 3 types:
Labels:
Hacking,
Tips And Tricks,
Tutorial
AVG Internet Security 2011/ 10.0.1209 Build 3533 Multilingual (x86/ x64)
AVG Internet Security 2011/ 10.0.1209 Build 3533 Multilingual (x86/ x64) | 171/193 Mb
Complete protection f everything you do! With AVG Internet Security our most advanced protection you get a wry-free online experience every time. This award-winning product gives you unbeatable Internet security by protecting against viruses spyware hackers spam and malicious websites. AVG Internet Security is a reliable and easy-to-use solution f home and small office users which is trusted by millions of users wldwide.
Thursday, 8 September 2011
Facebook Flooder (Post unlimited any text on your friends wall)

Want to flood someone's wall on facebook ????
looks like someone is annoying you ............ :D
Labels:
Facebook,
Facebook Hacking,
Learn,
Tips And Tricks
Facebook Cookie Stealing And Session Hijacking

The cookie which facebook uses to authenticate it's users is called "Datr", If an attacker can get hold of your authentication cookies, All he needs to do is to inject those cookies in his browser and he will gain access to your account. This is how a facebook authentication cookie looks like:
Cookie: datr=1276721606-b7f94f977295759399293c5b0767618dc02111ede159a827030fc;
Labels:
Facebook,
Facebook Hacking,
Hacking,
How to,
Tutorial
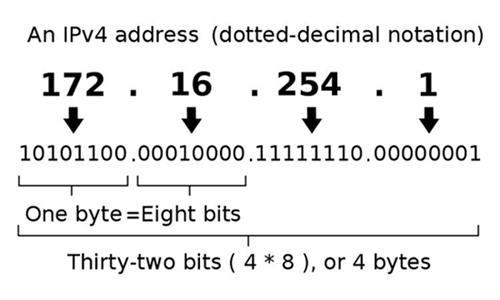
How to hack someone with their IP
Welcome to the basic NETBIOS document created by aCId_rAIn. This document will teach you some simple things about NETBIOS, what it does, how to use it, how to hack with it, and some other simple DOS commands that will be useful to you in the future. THIS DOCUMENT IS FOR NEWBIEZ ONLY!!! If you are NOT a newbie then don't go any farther reading this because if you're smart enough you probably already know it all. So don't waste yourt time reading something that you already know.
Internet Download Manager 6.07 + Patch.rar Full Crack
Internet Download Manager : The fastest download accelerator
Internet Download Manager (IDM) is a tool to increase download speeds by up to 500 percent, resume and schedule downloads. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. Simple graphic user interface makes IDM user friendly and easy to use.
Internet Download Manager has a smart download logic accelerator that features intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download accelerators and managers that segment files before downloading starts, Internet Download Manager segments downloaded files dynamically during download process. Internet Download Manager reuses available connections without additional connect and login stages to achieve better acceleration performance.
Internet Download Manager (IDM) is a tool to increase download speeds by up to 500 percent, resume and schedule downloads. Comprehensive error recovery and resume capability will restart broken or interrupted downloads due to lost connections, network problems, computer shutdowns, or unexpected power outages. Simple graphic user interface makes IDM user friendly and easy to use.
Internet Download Manager has a smart download logic accelerator that features intelligent dynamic file segmentation and safe multipart downloading technology to accelerate your downloads. Unlike other download accelerators and managers that segment files before downloading starts, Internet Download Manager segments downloaded files dynamically during download process. Internet Download Manager reuses available connections without additional connect and login stages to achieve better acceleration performance.
Wednesday, 7 September 2011
How to Hack a WEBSITE with DNN?
This is a really effective way of hacking a website. This way is very common and according to some research 10% of sites are vulnerable to this.
So to start first thing that we need is vulnerable site which can be found from the following dork :
inurl:"Fck/fcklinkgallery.aspx" (for all the sites)
inurl:"Fck/fcklinkgallery.aspx" site:{domain of site} (for specified attack)
So to start first thing that we need is vulnerable site which can be found from the following dork :
inurl:"Fck/fcklinkgallery.aspx" (for all the sites)
inurl:"Fck/fcklinkgallery.aspx" site:{domain of site} (for specified attack)
How to Hack Facebook, Myspace, Tagged, Orkut, Hotmail, Gmail.
Well this is the question in every bodies mind that how can we hack a email account or How do others do it. When I started reading about Hacking I also search about this question and search for the Soft wares that can do it for me but there was nothing that work. Then comes the websites like hackfacebook.net that claim to hack 98% of facebook accounts for only 140 euros. But that is a BIG FRAUD. So question comes to mind How do we Hack the Accounts.
In real there are 5 ways to hack any account and they all work but there are not easy and not 100% efficient but with time you can master them all. The ways Are
TrustPort Internet Security 2011 11.0.0.4615
TrustPort Internet Security 2011 11.0.0.4615 | 216.2 MB
TrustPort Internet Security 2011 - comprehensive protection for your computer and data from malware and Internet threats. Solution stops viruses and spyware at all points of access and prevents access to your computer from hackers. TrustPort Internet Security solution incorporates antivirus, antispyware, antispam, firewall, and protects your PC on all aspects of information security.
TrustPort Internet Security - a comprehensive anti-virus that detects viruses and spyware on all the lines of the system, and also prevents hackers access to your computer. The program effectively protect your computer from malicious software and online threats with any method of connection. TrustPort uses two antivirus engines: AVG and BitDefender with a choice of either of the two engines, or use both of two!
Tuesday, 6 September 2011
How To Get Windows 8 Interface Instantly On Your Windows 7 PC
Windows 8 is yet to release, but buzz has started regarding it. We bring you an opportunity to try its desktop interface. Note that, It’s not the OS. It is just an application that gives your PC a look that resembles with widget-based look of Windows 8. You should have Windows 7 and .Net Frame v4 installed on your PC. Now, follow the steps below:
Labels:
Downloads,
Free,
Tips And Tricks,
Tutorial,
Updating,
Windows 7 Genuine,
windows 8
Dangerous iPhone exploit code goes public
"Comex", the developer of JailbreakMe 2.0, posted source code for the hacks that leveraged two vulnerabilities in iOS and allowed iPhone owners to install unauthorized apps. Minutes after Apple issued a security update Wednesday, the maker of a 10-day-old jailbreak exploit released code that others could put to use hijacking iPhones, iPod Touches and iPads.
The exploits that comex used to jailbreak the iOS could be used for other purposes, including delivering malicious payloads to grab control of iPhones, iPads , and iPod Touches. All that would be necessary is for hackers to dupe users into visiting a malicious Web site or persuading them to click on a link in an e-mail or text message.
Labels:
Hacking News
Avast! Internet Security & Pro Antivirus v6.0.1091
Avast! Internet Security & Pro Antivirus v6.0.1091 Incl. Keys | 254 MB
avast! software provides complete virus protection for your computer. Antivirus engine is complemented by anti-spyware, firewall and antispam modules to protect you against phishing schemes, identity theft and internet-distributed web viruses. Automatic updates for greater user convenience and safety. Top user ratings among free antivirus software. The new avast! includes a spyware detection engine.
To protect you from identity theft as well as viruses. avast! Pro Antivirus - better protection during web surfing. Full-featured antivirus software. Better than our free antivirus, especially for web surfing, but without the firewall and antispam included in avast! Internet Security. Also if you wish to customize your security, this is the recommended software.
Kaspersky Internet Security 2011
Kaspersky Internet Security 2011 has everything you need for a safe and secure Internet experience.
The Kaspersky Internet Security application was designed to be a all-in-one security solution that offers a worry-free computing environment for you and your family. Kaspersky Internet Security has everything you need for a safe and secure Internet experience.
Features of "Kaspersky Internet Security 2011":
AVG Internet Security Business Edition 2011
AVG Internet Security Business Edition 2011 x64
AVG Internet Security Business Edition 2011
Ultimate endpoint security for your employeesâ
laptops and PCs File Server protection to prevent malware from spreading across your network
Email Server protection against spam, phishing and email threats
Automated Security Updates plus security monitoring and reporting
Screenshot
Avast! Internet Security 6.0
avast! Internet Security 6.0
avast! software provides complete virus protection for your computer. Antivirus engine is complemented by anti-spyware, firewall and antispam modules to protect you against phishing schemes, identity theft and internet-distributed web viruses. Automatic updates for greater user convenience and safety. Top user ratings among free antivirus software. The new avast! includes a spyware detection engine. To protect you from identity theft as well as viruses. avast! Pro Antivirus – better protection during web surfing. Full-featured antivirus software. Better than our free antivirus, especially for web surfing, but without the firewall and antispam included in avast! Internet Security. Also if you wish to customize your security, this is the recommended software.
Norton Internet Security 2012 Final Multi-Language
Norton Internet Security 2012 Final Multi-Language
The Internet is a dangerous place, and cybercriminals are getting more creative in ways to target you and your invaluable personal information. Norton Internet Security 2012 provides our most powerful virus, online and PC protection so you can do more without interruption.
Labels:
Antivirus
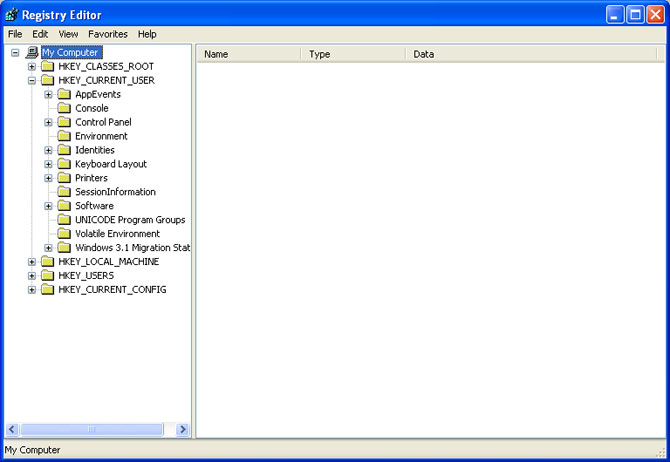
HOW TO ENABLE OR DISABLE REGEDIT IN YOUR SYSTEM
Enable or disable the gpedit of the system which is disabled by administrator or virus.It may difficult to install and register it in windows registry if the regedit is disabled.In most of the cases virus will disable the regedit.Here I am explainning how to enable or disable the regedit by the help of gpedit..
You have to follow the below procedure to enable or disable regedit in your system
You have to follow the below procedure to enable or disable regedit in your system
Labels:
Registry,
Tips And Tricks,
windows XP
Add Control Panel to your Desktop Right Click Menu
Adding an item to your right click menu of desktop allows you to access that item easily. You can add any item which you want to use frequently. Today i am writing a trick about adding control panel. If you want to add control panel to your right click menu of desktop as shown in figure. follow given steps below.
steps to add
Labels:
Tips And Tricks,
windows XP
Monday, 5 September 2011
Windows 8 Preview: 23 Potential Features You Should Know About
Still a year or more from final release, the next version of Windows has been making its fair share of appearances on leak sites in recent months. Codenamed Windows Next, the OS release we've come to know as Windows 8 will look much like its recent predecessors on the surface, but looks to be getting a serious revamp from the kernel up.
Labels:
windows 8
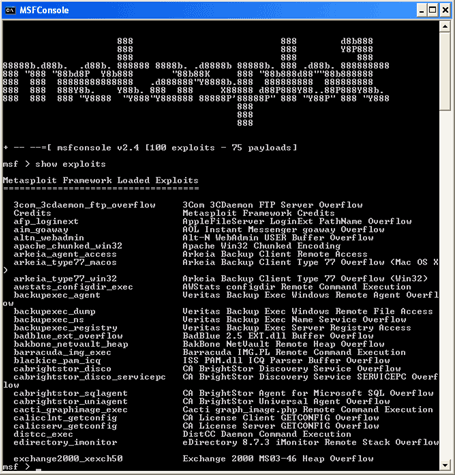
Hacking a remote computer or web server or your friend with Metasploit
Before continuing read our disclaimer
Metasploit is an Penetration testing tool by Rapid7
Download Metasploit here
Metasploit Download - Rapid7
Labels:
Hacking,
Metasploit,
Server
Make Your Windows 7 Genuine
Friends are you using windows 7 and want to make it genuine then download this and enjoy your windows 7 Genuine
Download http://www.mediafire.com/?w652b8c6ie99db6 (15.52 MB)
Download http://www.mediafire.com/?w652b8c6ie99db6 (15.52 MB)
Labels:
Windows 7 Genuine
How to run BackTrack 5 in Windows Virtual PC in Windows 7 | BackTrack 5 Tutoria
Got Windows and prefer using Windows Virtual PC over Virtual Box or VMWare then you are in the right place.
Download following
- Windows Virtual PC [validation required - if you do not have genuine windows download virtual PC here
- Backtrack 5 ISO -Gnome or KDE but NOT ARM
Labels:
Back Track 5,
Hacking,
Learn,
Video,
Virtual PC
SQL injection tutorial With Pictures
SQL injection is a code injection technique that exploits a security vulnerability occurring in the database layer of an application. The vulnerability is present when user input is either incorrectly filtered for string literal escape characters embedded in SQL statements or user input is not strongly typed and thereby unexpectedly executed. It is an instance of a more general class of vulnerabilities that can occur whenever one programming or scripting language is embedded inside another. SQL injection attacks are also known as SQL insertion attacks.
Labels:
Hacking,
Learn,
SQL Injection,
Tutorial
Subscribe to:
Posts (Atom)