Thursday 17 November 2011
Sunday 6 November 2011
Saturday 15 October 2011
How To Run A Trial Software Forever

Today i will show you two ways to hack software and run a trial software forever.
Most of us are familiar with many softwares that run only for a specified period of time in the trial mode.Once the trial period is expired these softwares stop functioning and demand for a purchase.But there are ways to run the softwares and make them function beyond the trial period.
Most of us are familiar with many softwares that run only for a specified period of time in the trial mode.Once the trial period is expired these softwares stop functioning and demand for a purchase.But there are ways to run the softwares and make them function beyond the trial period.
Friday 14 October 2011
Protect your Facebook account from hackers with MyPageKeeper Facebook Security Application Security Tips
acebook users can lean on a new app to help them fight spam and malware.

Designed by a team of students at the University of California at Riverside, MyPageKeeperis a free Facebook app that continually monitors wall posts and news feeds for malicious content. If the app suspects that any content may contain spam or malware, it alerts you and gives you the ability to remove it.

Designed by a team of students at the University of California at Riverside, MyPageKeeperis a free Facebook app that continually monitors wall posts and news feeds for malicious content. If the app suspects that any content may contain spam or malware, it alerts you and gives you the ability to remove it.
Labels:
Facebook,
Tips And Tricks,
Tutorial
How To Hack FaceBook Account Using A Web Based Exploit
Do you want to learn how to hack facebook?, Are you looking for a way to hack your friends facebook account without them fiding out? Interested in finding out ways to hack someones profile? Maybe you want to take a quick peek at their message inbox or use a glitch to use a hacking script. In this article I will show you a fairly easy step by step guide on how to hack facebook user accounts without having to directly hack into facebook and risk getting caught. Ignore all those hacking services, facebook hacks and hackers that charge you money for something you can do on your own for free. Hack the password of any of your friends accounts and get their password even as a prank or joke (you may also be interested in trying our How To Hack Twitter Accounts tutorial).
Hack facebook, hacking facebook passwords from user accounts and find out someones facebook password...Is any of it really possible? Yes it is, thanks to Twitter!. By now, you have probably heard the rumors of how unsafe Facebook is with a few celebrities having had their accounts hacked. You may also have seen Twitter allows you to synchronize your tweets with Facebook status updates so whatever you tweet appears as a Facebook status update. In providing this service, Facebook has created many vulnerabilities for itself by allowing a third party (Twitter) to access their database. This problem is due to Facebooks API service which permits exterior websites or applications (like FarmVille) to modify or post stuff on your profile.
A couple of month's ago I wanted to check my old FaceBook account but forgot what email and password I had used to sign up, I sent an email to their technical support but they didn't reply so I decided to put my geek skills to good use and find a way to get my login information back by writing a facebook account hacking code or exploit as they are called.
HOW HACKING FACEBOOK ACCOUNTS WORKS
Facebook has two databases (one for males and one for females users) where they keep all the information from their users, if you remember the email you use to login but forget your password, you can use the 'Forgot your password?' option, however if like me you don't have any of that information it's impossible to legally recover that account.
If you know anything about programming websites you know the 'Forgot your password?' service has to be in direct contact with the databases in order to send requests to retrieve the forgotten information for you, basically what that means is if you 'ask' the database for the login information with the right 'code' (in our case exploit), it will send you back that information.
So all I had to figure out is what the code was and what system they used to contact the databases through the 'Forgot your password?' service, after a few weeks of writing and testing codes I came up with the right one for the job and after doing a bit of research I learned FaceBook uses something similar to an email service to contact their databases.
For security reasons the databases are programmed to verify the account your requesting is actually yours and not someone elses so they need some type of authentication or verification (thats why they send you a verification link to your email when creating your account or changing your password).
Luckily for us, as mentioned above, through the use of Twitter combined with Facebooks 'Mutual Friend' feature, we can use a friends account to verify your own, in other words, if the person you want to get the login information from is on your friends list on Facebook...you can use your Twitter account to verify your their friend on Facebook taking advantage of the vulnerability of the twitter status sync exploit, and get their login email and password sent to you. But the victim must be on your friends list on Facebook.
HOW TO DO IT
1) First off you will need to get your user id and the victims user id, how do you do this?
Go to the victims profile, then click on their Display Picture (not the "View Photos of ..." link or tab but the actual main picture of their profile) and look at your browsers address bar, at the end of all the address you should see a group of numbers that should you should look something like this: (I have used a red arrow to point them out)
Don't worry if it isn't exactly like that (sometimes it has variations like; 'album.php?profile=10957800008') just as long as you get the numbers. Write them down somewhere as you will need to use it a bit further down, once that is done you may continue to step 2.
2) At the bottom of this page I have pasted the exploit code I created to fool the databases, this is the tricky part as you will have to edit the code a bit yourself so that it fits your needs when searching for the victims login information.
Scroll down to the bottom of this page and find the code I have highlighted in gray so you know what to copy, select the code and copy it to your clipboard (press CTRL+C) then paste it (CTRL+V) on a notepad or text document so you can edit it.
3) Once you have the code somewhere you can edit it, you will need to insert three things into it, the facebook user id of the victim and the twitter friend authentication information. I will give you step by step examples by trying the exploit code on my friend Laura's account as the victim, see what parts you have to edit and with what:
1. Should be the victims user id.
2. Should be your twitter login Username (I put my email in the screencap example above for privacy reasons) to verify your the victims mutual friend on facebook. Make sure your facebook email was the same used to sign up to Twitter so the exploit script can automatically connect both accounts.
3. Should be your twitter password so the database can authentic you really are friends with the victim on facebook.
When editing the code, don't accidentally delete one of the quotes (") or it won't work, so make sure you put the information inside them.
4) Now that you have the exploit code edited and ready to send, we are all set to send it to the database through an email, since it's not your regular email but an exploit email we will have to use a special Subject so the database knows how to read it in programming language.
Go to your email address and Compose a new email to fbsupport@techie.com which is their customer service email for forgotten passwords, in the Subject copy and paste the code below highlighted in gray:
$[search_database = $find user+id= "123456789", '%verification+user+bday' = }"01/01/1900"{ begin_search();
Once you have edited the Subject and entered the email address, your Composed email should look like the screenshot below, I will numerate each item:
1. The email address of the facebook database's forgotten password customer service.
2. This is where you insert the victims facebook user id.
3. This is where you insert your birthday so the database can find you to verify your a friend of the victim (it arranges users in the database based on your date of birth), NOTE: It MUST be in the MONTH/DAY/YEAR format so it can read it properly.
5) After you have correctly written the To: and Subject sections, you may proceed to insert the exploit code you previously edited in step 3 into the body section of the email.Now all you have to do is click Send and wait for the database to send you back it's reply with the information.
It should take from 12-24 hours depending on the traffic FaceBook has that day, this is a sample of the email response you'll receive:
THE EXPLOIT CODE
fb_select_db("find", $linkID) or die(fbdatabase_error());
$resultID = fb_query("SELECT FriendID FROM signup WHERE email = '$email'", $linkID) or die(fbdatabase_error());
$num_rows = db_num_rows($resultID);
$row = facebook_fetch_array($resultID);
$user_id = $row[0];
if ($user_id == "PUTUSERIDHERE") = '$repeat' {
print Success, We have sent you an email with the Login email and Password of that ID.
}
else {
// print "We're sorry, your friend ID does not appear to be in our database."
$passwordfromdb = $row[0];
$find userID = (%friend_list)
#forgot_pass_userid = "%repeat%"; <%search_database_for_id%>
#user email= "PUTEMAILHERE"; (%friend_vulnerability_email%)
#user password = "PUTPASSWORDHERE"; (%friend_vulnerability_pass%)
$friend_database_exploit = '%request_forgot_pass_info'
$email_to = %%%@subject_email
session_start();
session_reset_pass("session");
$email_address = $_POST['email_address'];
if (!isset($_POST['email_address'])) {
}
elseif (empty($email_address)) {
echo $empty_fields_message;
function decrypt userID password() {
$salt = "abchefghjkmnpqrstuvwxyz0123456789";
srand((double)microtime()*1000000);
$i = 0;
while ($i <= 7) {
$num = decrypt() % 33;
$tmp = substr($salt, $num, 1);
$pass = $pass . $tmp;
$i++;
}
return $pass;
}
mail($email_address, $subject, $message, "Facebook Password Reset Confirmation
}
/end$
Labels:
Facebook,
Facebook Hacking,
Free,
How to,
Tips And Tricks,
Tutorial
Thursday 13 October 2011
How To Recover Your Computer After Virus Attack (Re - Enable)
How To Recover Your Computer After Virus Attack
Even after the virus is totally removed from the system, some users find it difficult to restore all those things back which were affected by the virus. A virus usually when enters into a system disables the registry editor and task manager so that the user can not remove the virus from the system.
Here is a free tool Re-Enable using which even a novice users can fix all the things which were disabled by the virus. An antivirus can remove the virus files but sometimes it may fail to restore the system settings. In such situations this tool can come handy.
Portable Phase One CaptureOne Pro v6.2.49045.7

Portable Phase One CaptureOne Pro v6.2.49045.7
Portable Phase One CaptureOne Pro v6.2.49045.7 | 201.56 MB
The raw converter for ultimate image quality. Capture One Pro 6 is a professional RAW converter and image editing software. It contains all the essential tools and high-end performance in one package to enable you to capture, organize, edit, share and print images in a fast, flexible and efficient workflow. Capture One Pro 6’s powerful and intuitive toolset is used by professional photographers to achieve world-class image quality with excellent color and detail.
Wednesday 12 October 2011
How to Know if You Are Infected with RATs or Keyloggers
How to Know if You Are Infected with RATs or Keyloggers
In this post i am going to show you how to find out when you are infected with a RAT or Keylogger without using any complex tools. Now i believe most of you might know that you need to have an internet connection to make a RAT or a Keylogger work, which would mean, if you are not connected to internet, you don't have to worry about being infected with RAT or Keylogger Ok, so for those who have internet connection and think they are being infected with a Trojan, here is a little guide that can solve your problem.
Labels:
Free,
Hacking,
RAT Programming,
Tutorial
Download Keyscrambler Personal: Protect yourself from keyloggers
How to use Keyscrambler Personal:
1. Free download Keyscrambler Personal to protect yourself from keyloggers.
2. Install this Keyscrambler software on your computer and restart.
Tuesday 11 October 2011
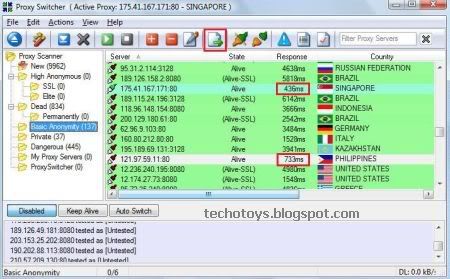
Download Proxy Switcher Standard: Free IP Changer | Hide your IP
Proxy Switcher is one of the best proxy softwares ever made and it is a perfect free IP Changer tool. This software automatically downloads and tests all proxy servers. So, you don’t need to search for any “free proxy list” on Google. This software can also automatically change your IP address every 5 minutes or so (available in Pro version) which makes it really useful.
Monday 10 October 2011
Sunday 9 October 2011
Saturday 8 October 2011
HACKING MSN – EASY WAY
Its basically a way of getting your email back if has been stolen, but I have come to realise that this to can be used to gain access to someones msn. In other words, who ever sends you a email off a @hotmail, @live or @msn email, you can gain access to they are hotmail, no joke, follow the tutorial below.
Friday 7 October 2011
Thursday 6 October 2011
Wednesday 5 October 2011
DVWA – SIMPLE WEBSITE HACKING TECHNIQUE EXPLAINED
Now many of you I think all want to learn hacking you read eBook and watch videos but what do you learn if you don’t use that knowledge on your practical work. If you hack a website than you may get caught so here in this tutorial I will tell you How to learn web hacking (with DVWA).
Before moving on first check that you have installed your server or not If you have not installed a Server in your PC than first read this “How to create your Home Server?” and come back.
Tuesday 4 October 2011
HACK ADMINISTRATOR PASSWORD IN WINDOWS XP, 7 & VISTA
if you did lost your password dont worry about this, just follow steps and login to ur admin.
You Need Blank Cd or floppy and internet Access Cd or floppy writer.
1. Download this small utility.
Click Here To Download
You Need Blank Cd or floppy and internet Access Cd or floppy writer.
1. Download this small utility.
Click Here To Download
Monday 3 October 2011
Saturday 1 October 2011
The Most Wanted Software Collection Mega Pack 2011
Installation Method
-Disable or block Internet
-Mount in virtual drive (UltraISO, Alcohol120%, DaemonTools etc), or extract the image to your hard drive, flash drive, external hard drive. You can also burn the image onto your blank DVD9 - it will have to remove some unwanted program
-Start Drive
-In the window, place a checkmark in the programs you want to install
-Click "Start Installation"
-After installation, be sure to restart your computer
-Enjoy!
Necessary explanations
Recommend that you install on a clean and original distribution Windows, we can not guarantee the program will work on any kind of assemblies and "cluttered" systems
Installation of some programs may take a long time and it may seem that the process is frozen, be patient and wait until the installation is complete, the list of programs and components included:
-. NET Framework
- Microsoft Office 2010
- Microsoft Office 2003
- ABBYY FineReader
- PROMT
- Adobe Asrobat
- Adobe Photoshop
- Adobe Illustrator
- CorelDraw
-Disable or block Internet
-Mount in virtual drive (UltraISO, Alcohol120%, DaemonTools etc), or extract the image to your hard drive, flash drive, external hard drive. You can also burn the image onto your blank DVD9 - it will have to remove some unwanted program
-Start Drive
-In the window, place a checkmark in the programs you want to install
-Click "Start Installation"
-After installation, be sure to restart your computer
-Enjoy!
Necessary explanations
Recommend that you install on a clean and original distribution Windows, we can not guarantee the program will work on any kind of assemblies and "cluttered" systems
Installation of some programs may take a long time and it may seem that the process is frozen, be patient and wait until the installation is complete, the list of programs and components included:
-. NET Framework
- Microsoft Office 2010
- Microsoft Office 2003
- ABBYY FineReader
- PROMT
- Adobe Asrobat
- Adobe Photoshop
- Adobe Illustrator
- CorelDraw
Friday 30 September 2011
Portable Ashampoo 3D CAD Professional v3.0.1 by Birungueta
![Ashampoo 3D CAD Professional v3.0.1 by Birungueta [Portable SW] Ashampoo 3D CAD Professional v3.0.1 by Birungueta [Portable SW]](http://lulzimg.com/i17/6fbb8e.jpg)
Portable Ashampoo 3D CAD Professional v3.0.1 by Birungueta | 880 MB
Genre: Portable
Genre: Portable
Ashampoo 3D CAD Professional - a comprehensive system of three-dimensional design of buildings, aimed at professional architects, builders, designers and engineers. The product offers a range of useful features and tools, including the ability to export and import of 3D-models in two-dimensional drawings of DXF / DWG and rapid exchange of architectural plans c other team members. With this toolkit specialists will prepare a clear plan for new construction or redevelopment on a conventional personal computer. Ashampoo 3D CAD Professional will solve a number of standard tasks of creating accurate floor plan to the arrangement of furniture and decorative objects. A list of enhancements in version Ashampoo 3D CAD Professional launches new module Window Construction Module, intended for the design of windows to order. A new plug-in CINEMA 4D Export can be used to convert 3D-projects in file format CINEMA 4D. Special mention deserves the opportunity to use facilities projects 3DS, 3D-DXF and VRML.
Thursday 29 September 2011
Anti Keylogger (and Keyscambler addons) Protect your passwords
These days Agents spy on u everywhere, in college, at work, maybe a trojan virus on your home PC which keylogs your paswords and mails it to someone else.
If u think u r being logged, try this:
Whenever u have to type a password, never type the complete password in one go, ie, if your password is WINDOWS, u should type NDOW, then move cursor to start of the password field using the mouse ONLY, then type WI, then move cursor to end using the mouse and type S. This way the logger will record your keystrokes as ndowwis instead of WINDOWS.
Haha, keylogger fooled.
Another method is the use of Virtual Keyboard.
go to Start->All Programs->Accessories->Ease of Access–>select On-Screen Keyboard
There are some softwares also which can do the work for you:
If u think u r being logged, try this:
Whenever u have to type a password, never type the complete password in one go, ie, if your password is WINDOWS, u should type NDOW, then move cursor to start of the password field using the mouse ONLY, then type WI, then move cursor to end using the mouse and type S. This way the logger will record your keystrokes as ndowwis instead of WINDOWS.
Haha, keylogger fooled.
Another method is the use of Virtual Keyboard.
go to Start->All Programs->Accessories->Ease of Access–>select On-Screen Keyboard
There are some softwares also which can do the work for you:
Labels:
Free,
How to,
Tips And Tricks,
Tutorial
HOW TO HACK A FACEBOOK ACCOUNT USING TABNABBING With Video Tutorial
Requirements:
1. Phishing Pages by Hacking Loops: Click here to download
2. Register on my3gb website and upload these to them.
3. Send the link to victim.
Labels:
Facebook,
Facebook Hacking,
Free,
Tips And Tricks,
Tutorial,
Video
Wednesday 28 September 2011
Adobe Photoshop Portable AIO CS1 - CS5 (2011)

Adobe Photoshop Portable AIO CS1 - CS5 (2011) | 351 MB
Adobe Photoshop has all the methods of working with bitmaps, in this case is to work with layers and uses the contours. Adobe Photoshop is the undisputed leader among the professional graphic editors due to its widest possibilities, high efficiency and speed. Adobe Photoshop Portable AIO 2011 contains all of the portable version of Photoshop CS1 to CS5.
Hack Computer/pc using ip Adress
Literally, hacking is accessing something or somebody in internet without their permission or interest. While, speaking in summary, hacking is very easy job, it is like instead of using front door, finding the hidden door of a house and hijacking the precious things. Among all the hacking, hacking via IP address is one of the most common yet powerful beginning.
You may want to hack the website and put your advertisement there or grab some database information In this type of hacking, you are playing with the web server’s computer instead of the administrator’s computer. Because, www.website.com is hosted in separate web server rather than personal computer.
Another can be accessing your friend’s computer from your home. Again this is IP based and this is possible only when your friend’s computer is online. If it is off or not connected to internet then remote IP hacking is totally impossible.
Well, both of the hacking has the same process. Let’s summarize what we must do.
You may want to hack the website and put your advertisement there or grab some database information In this type of hacking, you are playing with the web server’s computer instead of the administrator’s computer. Because, www.website.com is hosted in separate web server rather than personal computer.
Another can be accessing your friend’s computer from your home. Again this is IP based and this is possible only when your friend’s computer is online. If it is off or not connected to internet then remote IP hacking is totally impossible.
Well, both of the hacking has the same process. Let’s summarize what we must do.
Sunday 25 September 2011
Ardamax Keylogger v3.8.5 Latest [Full] [Free] [Crack] [Serial Key]

Ardamax Keylogger is a keystroke recorder that captures user's activity and saves it to an encrypted log file. The log file can be viewed with the powerful Log Viewer. Use this tool to find out what is happening on your computer while you are away, maintain a backup of your typed data automatically or use it to monitor your kids. Also you can use it as a monitoring device for detecting unauthorised access. Logs can be automatically sent to your e-mail address, access to the keylogger is password protected. Besides, Ardamax Keylogger logs information about the Internet addresses the user has visited.
This invisible spy application is designed for 2000, XP, 2003, Vista and Windows 7.
Labels:
Downloads,
Free,
Hacking,
RAT Programming,
Tutorial
Thursday 22 September 2011
PC Tools Internet Security 2011 v8.0.0.651 (x32/x64) - Silent Installation
PC Tools Internet Security 2011 v8.0.0.651 (x32/x64) - Silent Installation | 84 MB
PC Tools Internet Security 2011 - Complete computer protection against spyware, adware, trojans, viruses, worms, keyloggers, browser hijackers, the false anti-spyware, phishing scams, unwanted programs, pop-up ads, hackers, malicious websites.
Detects, removes and blocks all types of viruses, Trojans, hacker attacks, illegal intrusions and other threats bezopasnosti.Samaya effective protection against spyware. Millions of users worldwide. In PC Tools Internet Security includes Spyware Doctor, the world's leading anti-spyware programs. Only Spyware Doctor has been downloaded over 100 million times. Every week this figure is increasing by one million. Millions of people worldwide use Spyware Doctor to protect their computers and the preservation of confidential information.
Sunday 18 September 2011
Wednesday 14 September 2011
TrustPort Total Protection v11.0.0.4615 Final (2011)
TrustPort Total Protection v11.0.0.4615 Final (2011) | 224.3 MB
TrustPort Total Protection 2011 - Maximum protection for your computer against malicious programs, Internet threats and identity theft. The program protects your computer from viruses and spyware at all access points. All e-mail and Web sites are checked to detect malware or unwanted content. Provides reliable protection of confidential data through encryption and secure deletion of sensitive data that are no longer used.
TrustPort Total Protection protects your computer from malicious software, online threats and data theft. Decision TrustPort Total Protection includes antivirus, antispam, firewall and data encryption, and provides full protection for your PC.
Tuesday 13 September 2011
Sunday 11 September 2011
How To Download Torrent File Using IDM
Yes… Its possible. Even when for the first time i thought of it, it was a day dream for me !
However, I got to know about this essential and important trick and i feel that everybody should be aware of this much needed downloading trick.
Also its very very simple to operate. Just you need to follow the steps below.
How to Change the colour of FACEBOOK!!!
 It is really interesting and easy to change the colour of the Facebook. The first thing you should have is FireFox.
It is really interesting and easy to change the colour of the Facebook. The first thing you should have is FireFox.Step 1) Download Greasemonkey, by searching the Google for it.
Labels:
Facebook,
Tips And Tricks
Saturday 10 September 2011
IStealer 3.0 [Tutorial] [Download]
![[Image: istealer.jpg]](http://img26.imageshack.us/img26/9679/istealer.jpg)
Before we start, I just wanted to say this, This is tutorial for people which have no knowledge on configuring a iStealer server! If you have no knowledge on how to configure a iStealer server please read on!!
Also before we start we need to sign up for a free FTP service, I currently usehttp://www.drivehq.com so use that one, sign up and now lets start!
Labels:
Downloads,
Free,
Hacking,
RAT Programming,
Software
Avast! Free Antivirus 6.0.989 Beta
Avast! Free Antivirus - Free Antivirus Avast, whose work is based on a number of award-winning antivirus kernel of avast!, includes all the features that you would expect from a modern antivirus program. In particular, it includes technology to protect against "spyware, " a certified West Coast Labs Checkmark, module protection against rootkits and reliable self-defense module. And the latest version provides even more high speed scanning and advanced malware detection. The program includes several of real-time "screens" that continuously monitor your email and connect to the Internet, checking the files to your computer every time they are opened or closed.
Antivirus avast! Free Antivirus is equipped with a completely revamped user interface that greatly simplifies the anti-virus scanning. With proper use Avast in conjunction with programs such as utilities for data backup, the program significantly reduces the risk that your computer is exposed to viruses or will be infected by them.
TrustPort Antivirus 2011
TrustPort Antivirus (2011) v11.0.0.4615 Final | 193.7 MB
TrustPort Antivirus 2011 - is a universal dvuskanernym antivirus solution that can withstand millions of spreading worldwide network of Internet threats - viruses, worms, spyware and Trojans. Due to regular updating of anti-virus and universal technology heuristics, TrustPort Antivirus has stopped suschestvuyushie malware, and those that will be created.
Friday 9 September 2011
REFOG Keylogger v6.0.4.1014 + Serial [ Full Version ] [Crack]
Concerned About Your Children Safety?
If your kids spend time chatting or playing computer games, they can be approached or threatened by the strangers. Internet has anonymity, and anonymity means impunity in the minds of molesters. The solution? Violate their anonymity by monitoring your kids’ activities!
REFOG Personal Monitor is designed to deal with extended families, but it fits small families just as easy. Allowing you to monitor your children activities remotely over the Internet, REFOG Personal Monitor does not even require your close presence in order to be alerted about suspicious activities of either your children or someone they chat with.
Hiren’s BootCD 13.2

Genre: SYSTEM Tools
Hiren's Boot CD is a boot CD containing various diagnostic programs such as partitioning agents, system performance benchmarks, disk cloning and imaging tools, data recovery tools, MBR tools, BIOS tools, and many others for fixing various computer problems. It is a Bootable CD; thus, it can be useful even if the primary operating system cannot be booted. Hiren's Boot CD has an extensive list of software. Utilities with similar functionality on the CD are grouped together and seem redundant; however, they present choices through UI differences.
Changes From Version 13.1 to 13.2
New Added Softwares:
Labels:
Downloads,
Free,
Hiren Boot CD,
Tools
Advance SQL Injection - 17 DefCon [Video]
According to OWASP top 10 vulnerabilities of 2010, SQL injection is the most dangerous and most common vulnerability around, A SQL Injection vulnerability occurs due to improper input validation or no input validation at all, what I mean by improper or no input validation is the user input is not filtered(for escape characters) before it gets passed to the SQL database, A Sql injection attack can be any many forms, but it's usually categorized into 3 types:
Labels:
Hacking,
Tips And Tricks,
Tutorial
AVG Internet Security 2011/ 10.0.1209 Build 3533 Multilingual (x86/ x64)
AVG Internet Security 2011/ 10.0.1209 Build 3533 Multilingual (x86/ x64) | 171/193 Mb
Complete protection f everything you do! With AVG Internet Security our most advanced protection you get a wry-free online experience every time. This award-winning product gives you unbeatable Internet security by protecting against viruses spyware hackers spam and malicious websites. AVG Internet Security is a reliable and easy-to-use solution f home and small office users which is trusted by millions of users wldwide.
Thursday 8 September 2011
Facebook Flooder (Post unlimited any text on your friends wall)

Want to flood someone's wall on facebook ????
looks like someone is annoying you ............ :D
Labels:
Facebook,
Facebook Hacking,
Learn,
Tips And Tricks
Facebook Cookie Stealing And Session Hijacking

The cookie which facebook uses to authenticate it's users is called "Datr", If an attacker can get hold of your authentication cookies, All he needs to do is to inject those cookies in his browser and he will gain access to your account. This is how a facebook authentication cookie looks like:
Cookie: datr=1276721606-b7f94f977295759399293c5b0767618dc02111ede159a827030fc;
Labels:
Facebook,
Facebook Hacking,
Hacking,
How to,
Tutorial
Subscribe to:
Posts (Atom)